Backdoor in upstream xz/liblzma leading to ssh server compromise
On March 29th, 2024, a new backdoor discovered in the xz/liblzma library has raised alarms across the tech industry, especially among those relying on Secure Shell (SSH) servers for secure communication. This backdoor poses a significant threat by potentially allowing unauthorized access to SSH servers, compromising their security and integrity.
Since this vulnerability was introduced in an upstream repository (i.e. liblzma), this represents a perfect example of the dangers of software supply chain risk.
Is Opvizor software affected?
Important: The Opvizor team immediately double-checked our infrastructure setup and the application deployment and nothing is affected by the xz vulnerability.
Understanding the Vulnerability
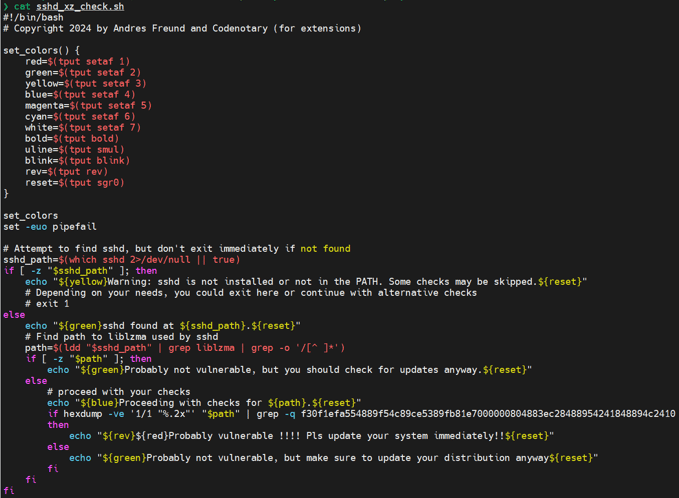
xz is a lossless compression program and file format which incorporates the liblzma library for compression algorithms. It is widely used in various Unix-like operating systems for file compression and decompression. The backdoor in question was ingeniously inserted in a manner that it could escape detection during routine security audits, making it a particularly stealthy threat.
The vulnerability arises when the compromised version of xz/liblzma is used to compress or decompress files. Specifically, the backdoor can be triggered, providing attackers with a way to execute arbitrary code. The OpenSSH remote logon software uses compression extensively and as such it is directly affected by this supply chain attack, which means that attackers could potentially gain unauthorized access to the server, execute commands, or even escalate their privileges to gain complete control over the system.
How can you protect yourself from this very significant new supply chain attack?
Please read more here at the Codenotary post, also how you can detect if you are affected by the vulnerability:
https://codenotary.com/blog/backdoor-in-upstream-xz